Web Proxy¶
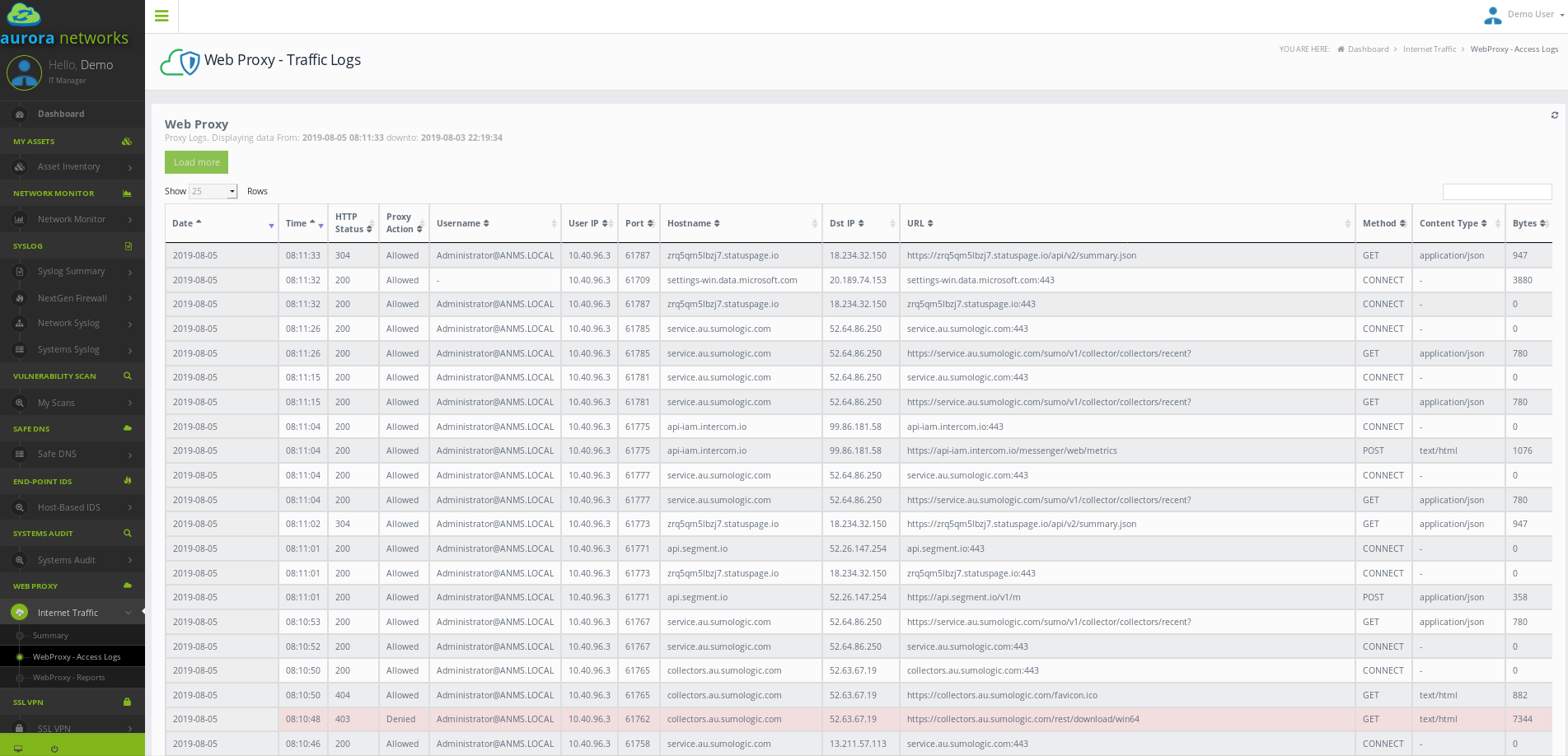
Service Requirements and Dependencies¶
Text
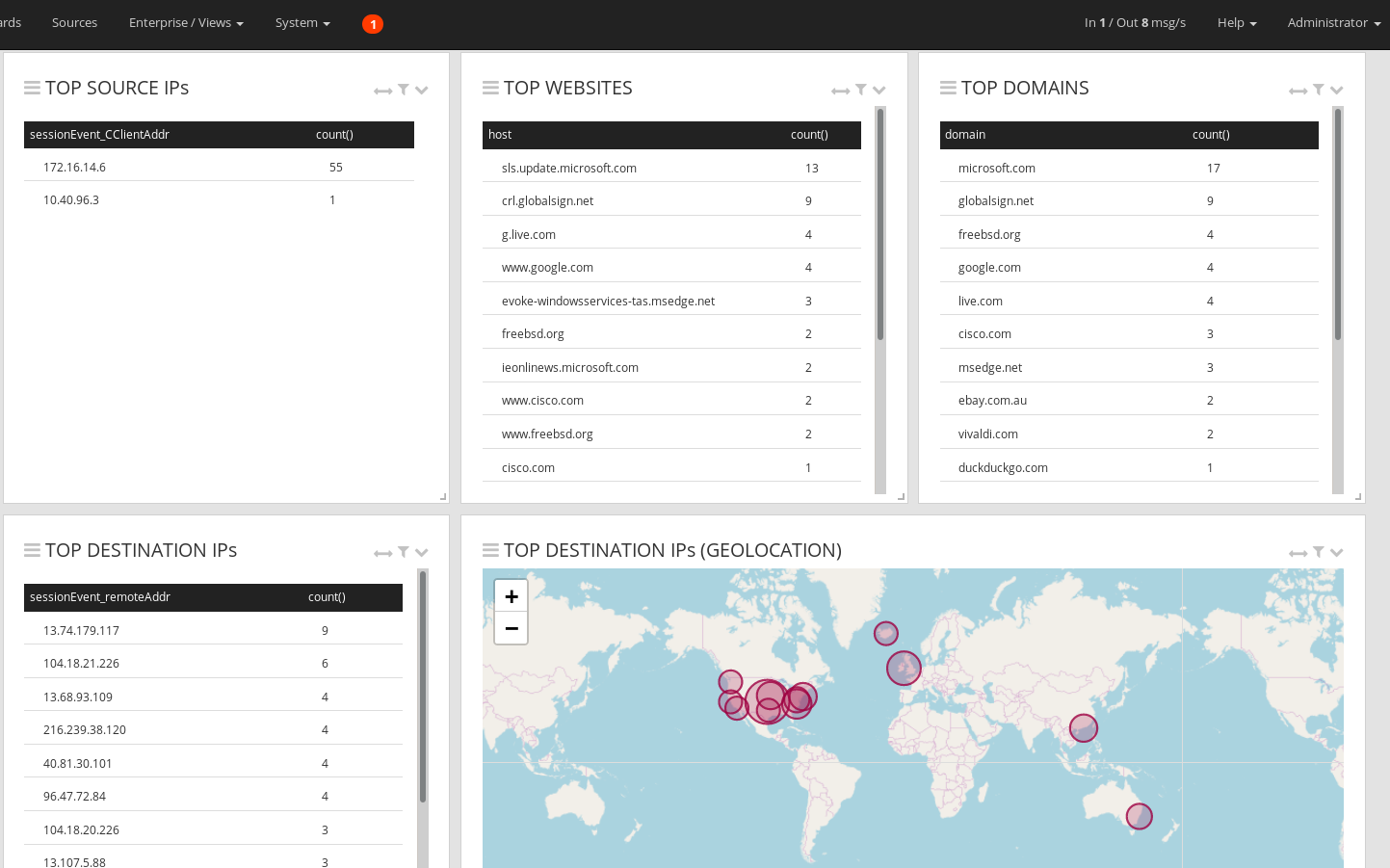
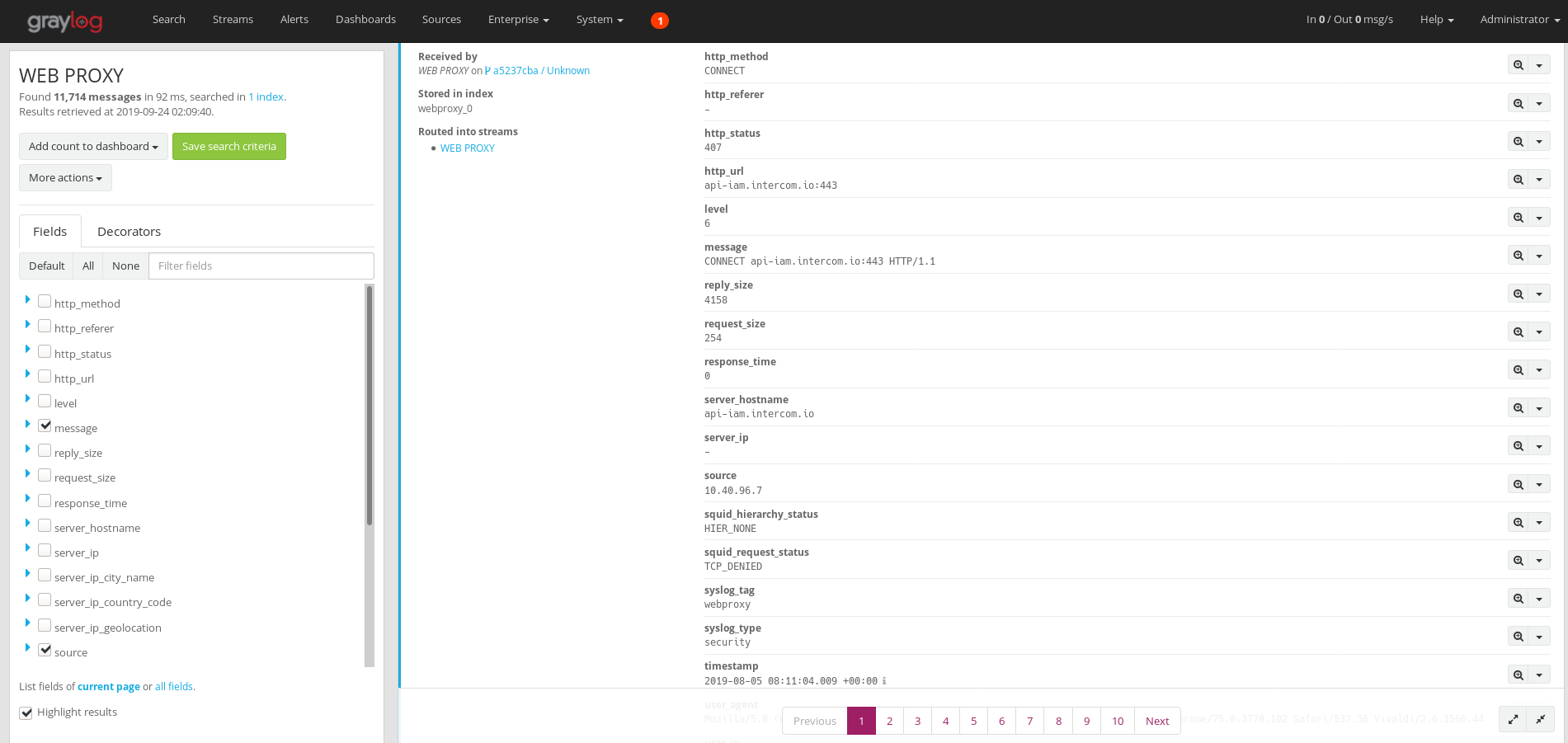
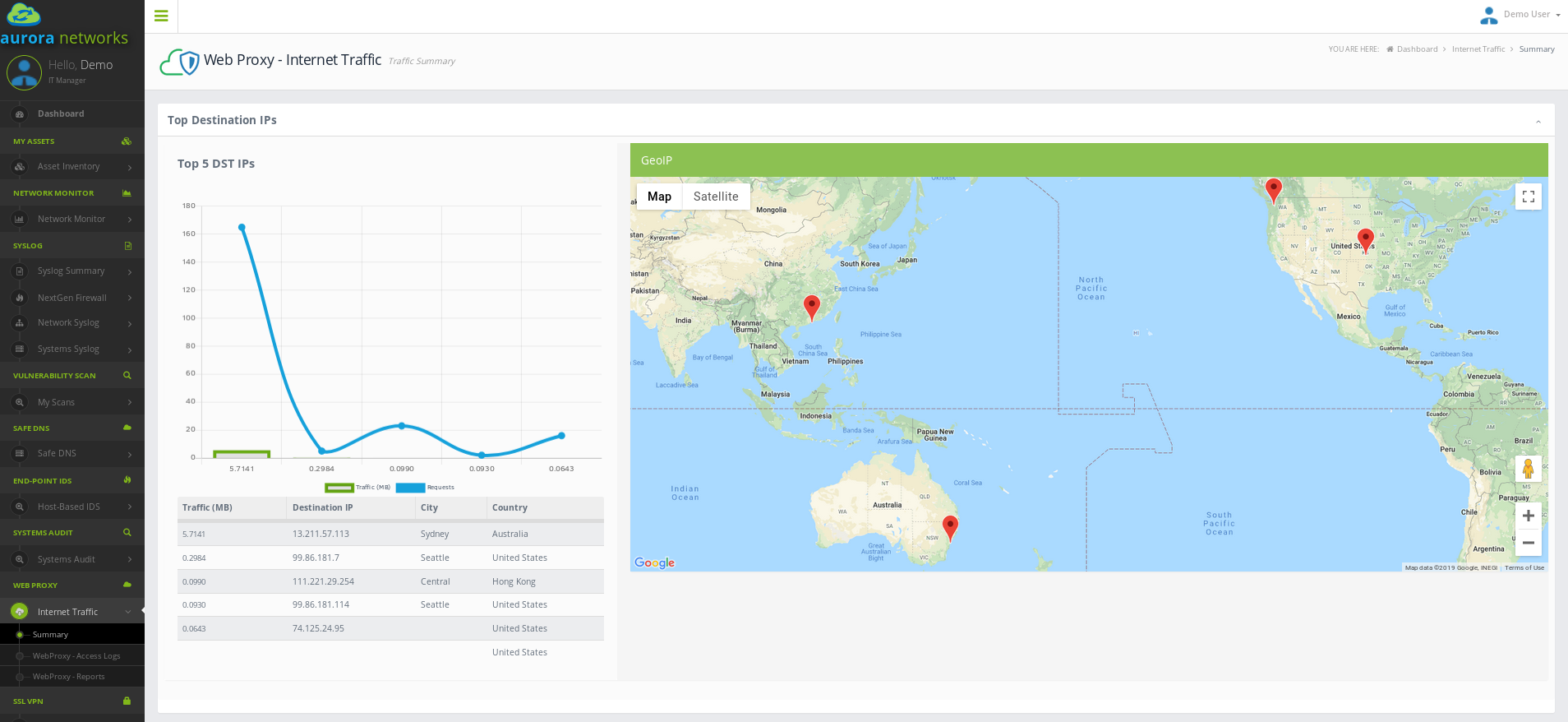
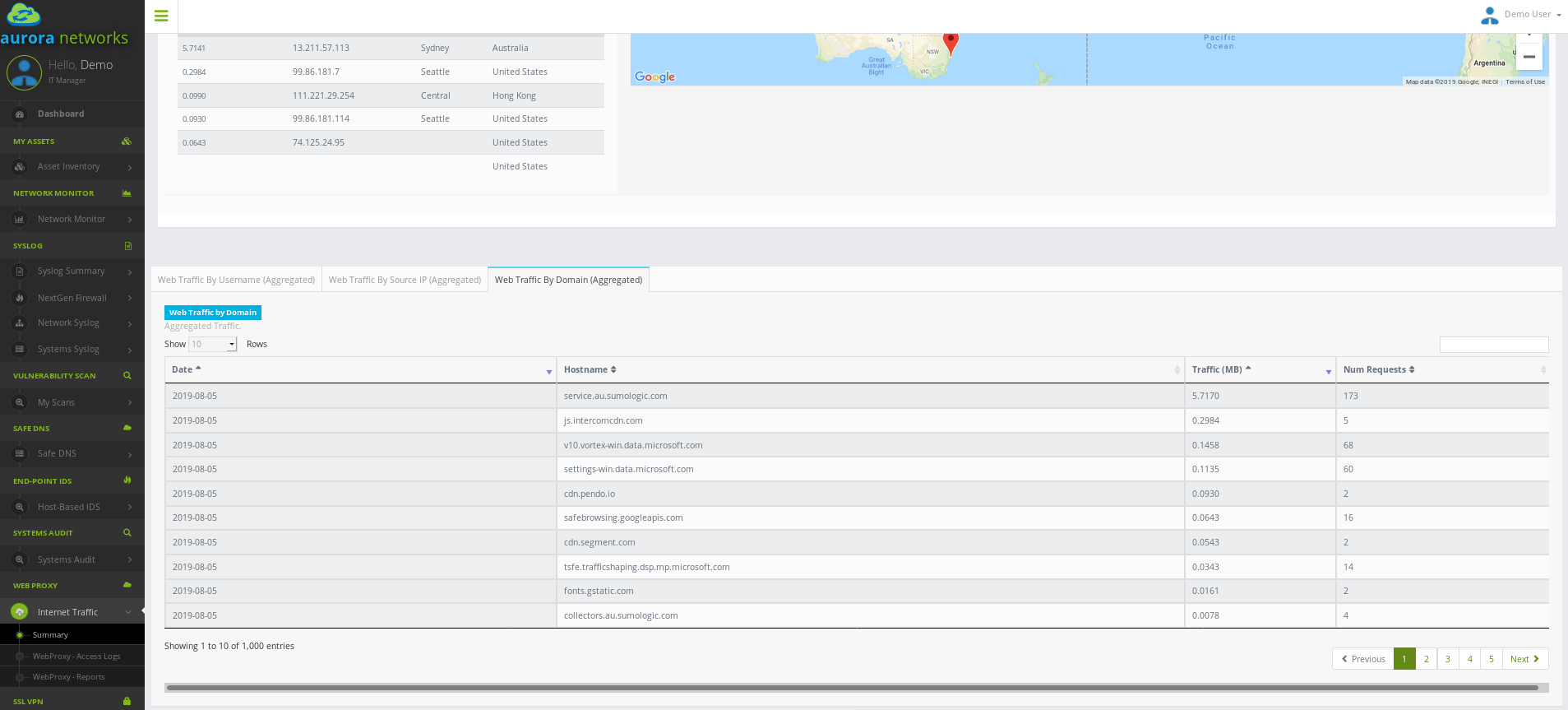
Service Overview¶
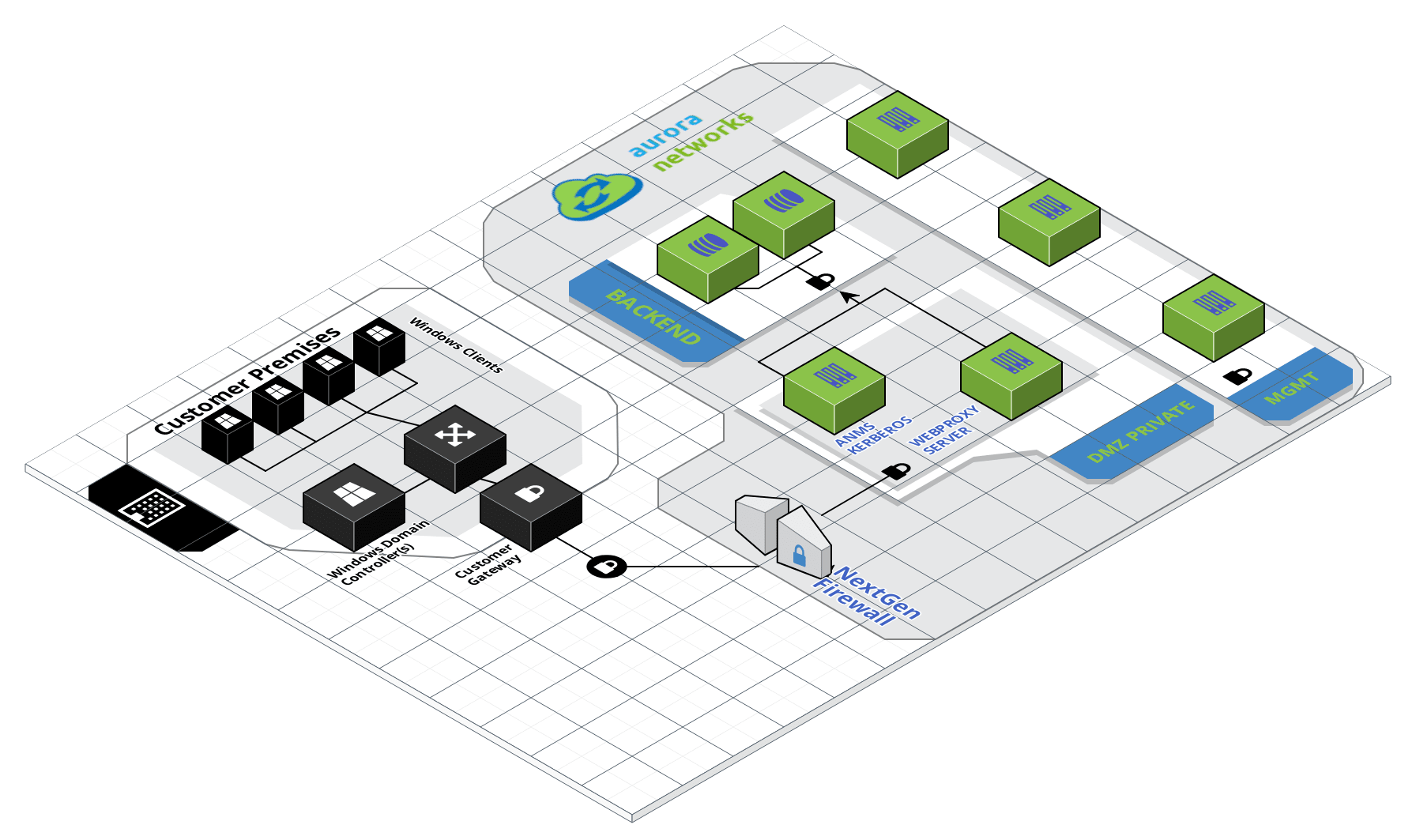
Kerberos Realm Trust - ANMS.LOCAL¶
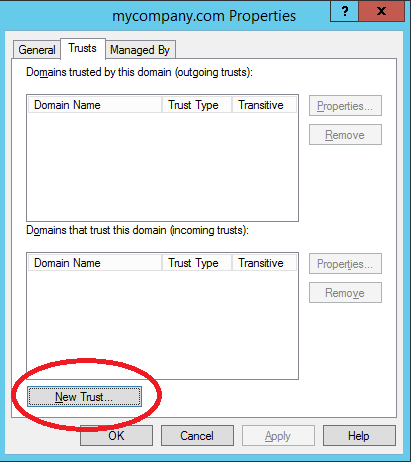
Open Server Manager and select Tools –> Active Directory Domains and Trusts. Once there select the Trusts tab and New Trust to launch the wizard:
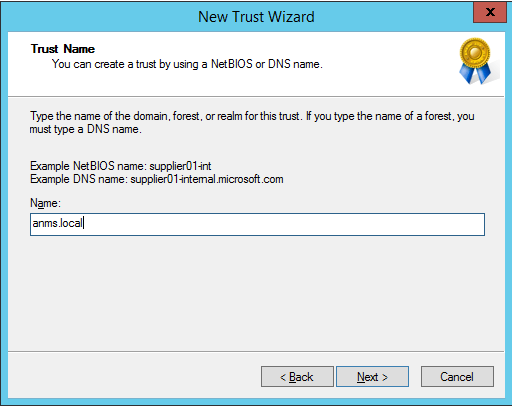
Type the target domain for this trust, anms.local:
Select Realm Trust:
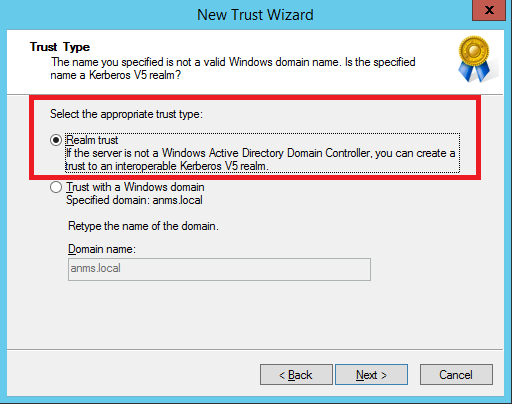
This trust will be Nontransitive:
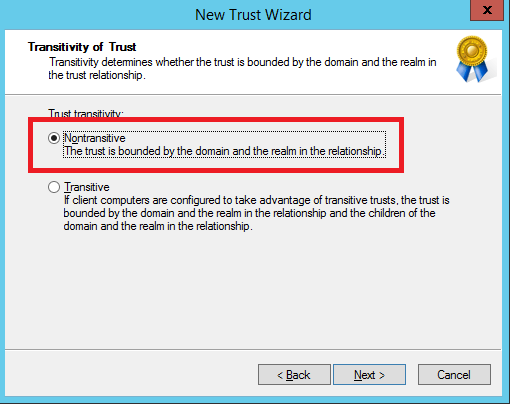
Select One-way: Incoming for the direction of this trust:
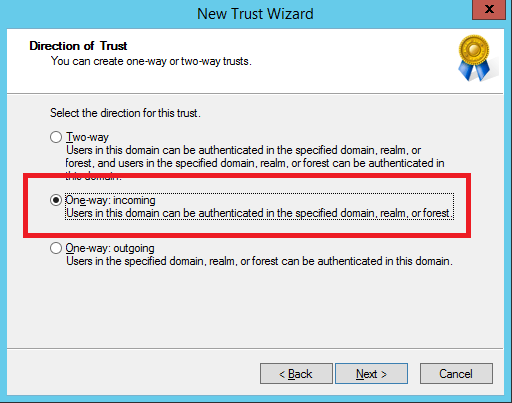
All trusts neeed to be confirmed by a Trust Password. This password will be communicated by ANMS:
Verify trust configuration:
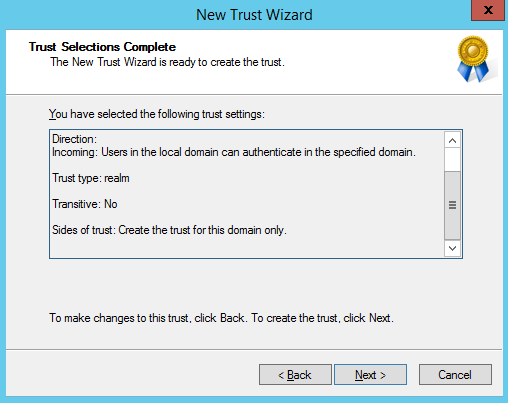
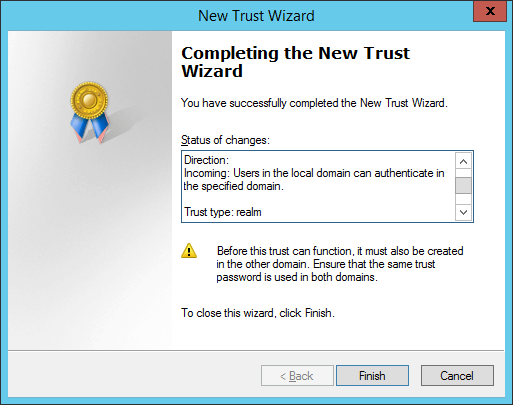
Confirm realm trust and complete configuration:
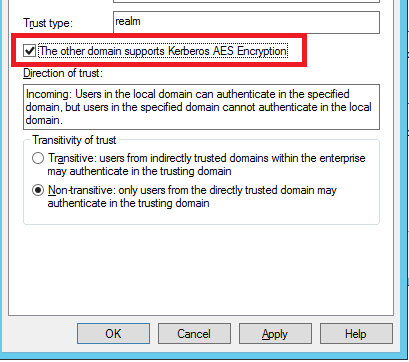
Once the realm trust has been configured open its properties and enable “AES Encryption”
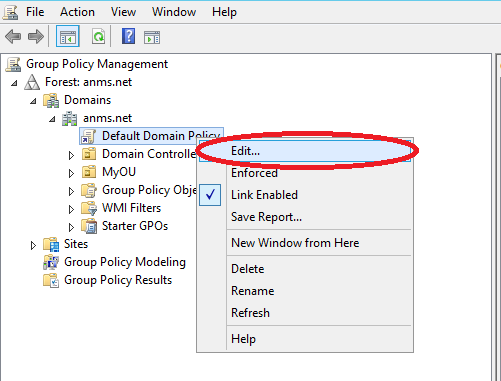
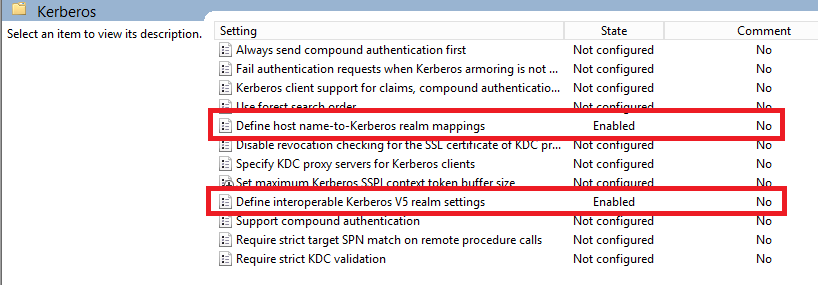
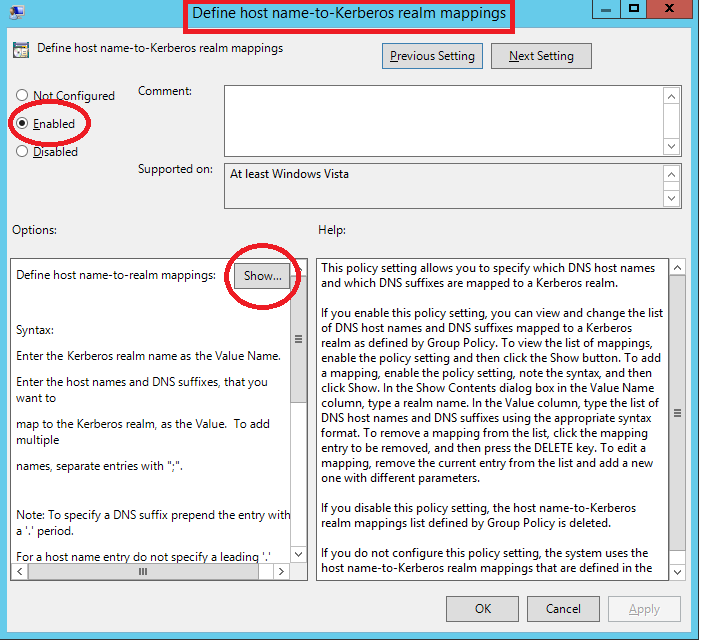
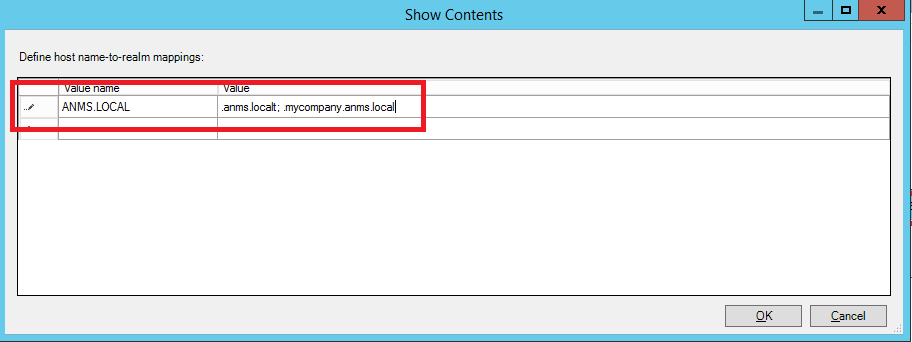
Kerberos Realm Trust - Group Policy¶
Open Server Manager and select Tools –> Group Policy Management. Edit desired domain policy:
Text
Text
Text
Text
Text
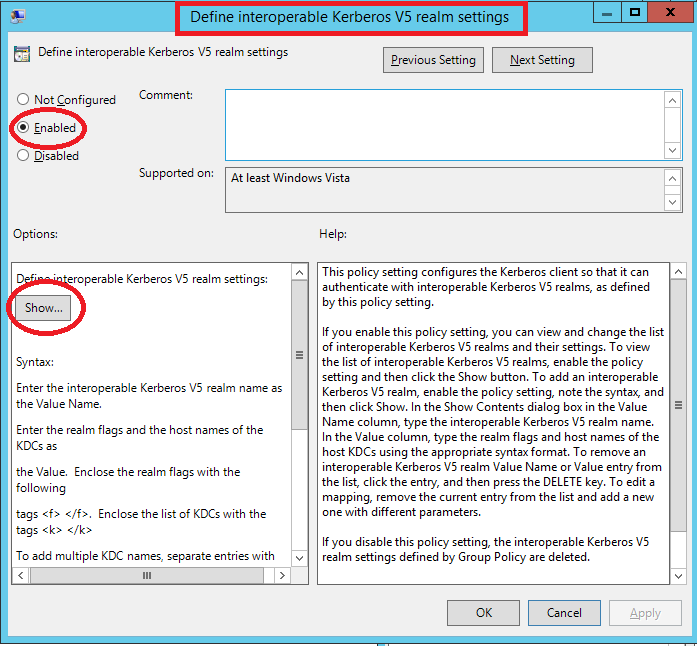
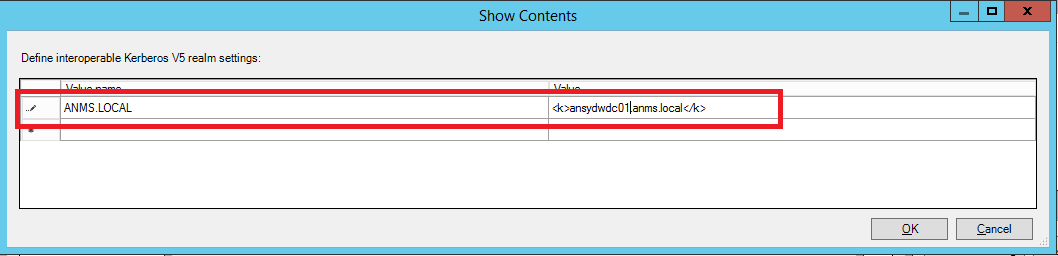
Text
Proxy PAC File¶
Text
function FindProxyForURL(url, host)
{
var proxy = "PROXY webproxy.mycompany.anms.local:8080; DIRECT";
var direct = "DIRECT";
// No proxy for private IP Addresses:
if (isInNet(host, "10.0.0.0", "255.0.0.0") ||
isInNet(host, "172.16.0.0", "255.240.0.0") ||
isInNet(host, "192.168.0.0", "255.255.0.0"))
{
return direct;
}
// No proxy for non-routable addresses (RFC 3330):
else if (isInNet(host, "0.0.0.0", "255.0.0.0") ||
isInNet(host, "127.0.0.0", "255.0.0.0") ||
isInNet(host, "169.254.0.0", "255.255.0.0") ||
isInNet(host, "192.0.2.0", "255.255.255.0") ||
isInNet(host, "192.88.99.0", "255.255.255.0") ||
isInNet(host, "198.18.0.0", "255.254.0.0") ||
isInNet(host, "224.0.0.0", "240.0.0.0") ||
isInNet(host, "240.0.0.0", "240.0.0.0"))
{
return direct;
}
// Proxy HTTP, HTTPS only:
else if (url.substring(0, 5) == "http:")
{
return proxy;
}
else if (url.substring(0, 6) == "https:")
{
return proxy;
}
else
{
return direct;
}
}
Firewall Rules¶
| Source | Destination | Protocol | Port | Direction |
|---|---|---|---|---|
| All Proxy Clients | ANMS Proxy Pac Server | TCP (HTTP) | 80 | Outbound |
| All Proxy Clients | ANMS Web Proxy Server | TCP | 8080 | Outbound |
| All Proxy Clients | ANMS Kerberos KDC | TCP and UDP | 88 | Outbound |
| ANMS Kerberos KDC | Your Windows DC | TCP and UDP | 389 | Inbound |
| ANMS Kerberos KDC | Your Windows DC | TCP | 445 | Inbound |