Web Application Firewall (WAF)¶
Intro¶
Aurora Networks Web Application Firewall (WAF) service is based on:
Network IPS at TCP/IP transport layers.
Anti-Malware Detection Engine.
Advanced Persistent Threat (APT) engine.
Apache Web Server acting as a Reverse Proxy.
Apache “ModSecurity” module.
OWASP Core Rule Set (CRS).
We are configuring a reverse proxy protecting access to your web server(s) and shielding the application server from the internet. In doing so, we’ll enable several configuration methods and will be working with ModRewrite and other modules available in apache web server.
Only Aurora Networks WAF (reverse proxy) is exposed to the Internet. Once the web application firewall has been setup it will conduct security checks on the HTTP payload and will forward the requests found to be good to your web server, hosted in your own premises or anywhere else.
For HTTPS access, the WAF also provides the first look into the encrypted requests. There are a number of ways for converting an Apache server into a reverse proxy. More importantly, there are multiple ways of communicating with the application server. Aurora Networks WAF uses the normal HTTP-based mod_proxy_http only.
Service Overview¶
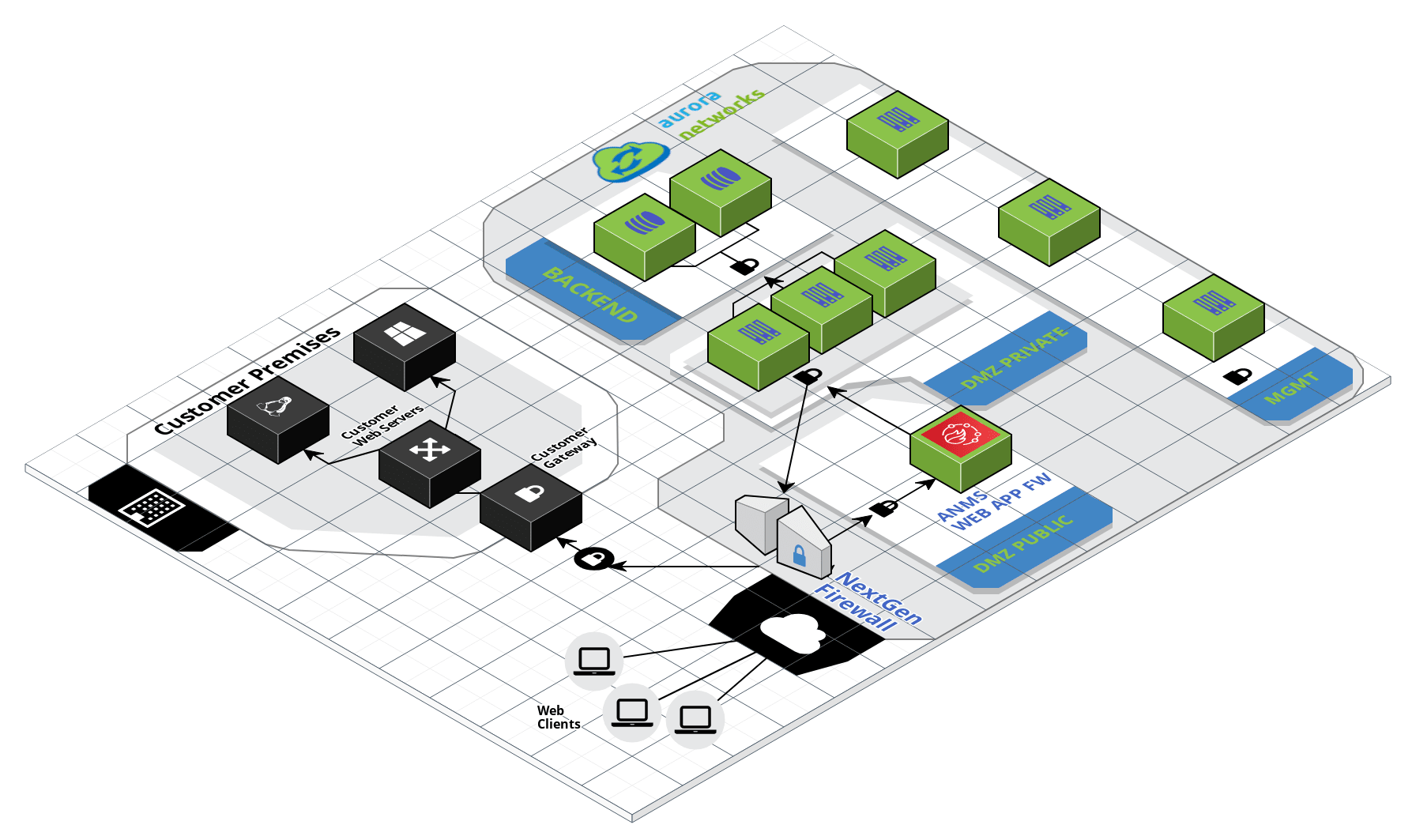
Web Requests and Traffic Flow¶
All HTTP and HTTPS requests to your web servers will ingress Aurora Networks VPC via a NextGen Firewall. The traffic will be decrypted and IPS policies will be enforced at the transport layer. This first security layer will block well-known, well-recognised malicious patterns by the inspection engine. Legitimate web requests will be checked against Apache’s HTTP ModSec module. In this second stage the HTTP payload is inspected and the OWASP Core Rule Set is evaluated. As part of this rule set Aurora Networks maintains a “black list” of source IPs that will be blocked without their traffic being even analysed. The way this black list is updated and maintained can be found later in this section.
After the web requests have passed through the application firewall legitimate requests are finally directed to your web server(s). The WAF will send back a HTTP 403 status message for all blocked requests.
Apache ModSecurity¶
Apache ModSecurity, sometimes called Modsec, is an open-source web application firewall (WAF). Originally designed as a module for the Apache HTTP Server, it has evolved to provide an array of Hypertext Transfer Protocol request and response filtering capabilities along with other security features across a number of different platforms including Apache HTTP Server, Microsoft IIS and NGINX. The platform provides a rule configuration language known as ‘SecRules’ for real-time monitoring, logging, and filtering of Hypertext Transfer Protocol communications based on user-defined rules. ModSecurity is most commonly deployed to provide protections against generic classes of vulnerabilities using the OWASP ModSecurity Core Rule Set (CRS). This is an open-source set of rules written in ModSecurity’s SecRules language. The project is part of OWASP, the Open Web Application Security Project. Several other rule sets are also available.
To detect threats, the ModSecurity engine is deployed embedded within Aurora Networks reverse-proxy in front of your web application. This allows the engine to scan incoming HTTP communications to the upstream endpoint (web server). Dependent on the rule configuration the engine will decide how communications should be handled which includes the capability to pass, drop, redirect, return a given status code, execute a user script, and more.
Open Web Application Security Project (OWASP)¶
The Open Web Application Security Project (OWASP), an online community, produces freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security.
The OWASP Foundation, a 501(c)(3) non-profit organization (in the USA) established in 2004, supports the OWASP infrastructure and projects. Since 2011, OWASP is also registered as a non-profit organization in Belgium under the name of OWASP Europe VZW.
OWASP is an open community dedicated to enabling organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted. OWASP Top 10 is the list of top 10 application vulnerabilities along with the risk, impact, and countermeasures. The list is usually refreshed in every 3-4 years.
OWASP Core Rule Set¶
The OWASP ModSecurity Core Rule Set (CRS) is a set of generic attack detection rules for use with ModSecurity or compatible web application firewalls. The CRS aims to protect web applications from a wide range of attacks, including the OWASP Top Ten, with a minimum of false alerts.
The Core Rule Set provides protection against many common attack categories, including:
- SQL Injection (SQLi).
- Cross Site Scripting (XSS).
- Local File Inclusion (LFI).
- Remote File Inclusion (RFI).
- Remote Code Execution (RCE).
- PHP Code Injection
- HTTP Protocol Violations.
- HTTPoxy.
- Shellshock.
- Session Fixation.
- Scanner Detection.
- Metadata/Error Leakages.
- Project Honey Pot Blacklist.
- GeoIP Country Blocking.
Threat Indicators and Security Feeds¶
All web activity and logs from Aurora Networks WAFs is sent to Graylog Centralised Log Management for your own information and analysis. The Threat Intelligence Plugin included in Graylog is used against all source IPs where traffic to your web servers is coming from.
Every time a threat condifion is flagged Aurora Networks SOC receives an alert with all relevant information about:
- Source IP triggering the threat condition.
- Country.
- Threat Indicator.
- Threat type (web scanner, honeypot, etc).
This information is checked against ThreatConnect (https://threatconnect.com) and if confirmed the WAF’s black list is updated accordingly.
Aurora Networks is also submitting detected threats and indicators to ThreatConnect for evaluation and security feed updates.
Firewall Rules¶
| Source | Destination | Protocol | Port | Direction |
|---|---|---|---|---|
| ANMS Web APP FW | Your Web Servers | TCP (HTTP/HTTPS) | 80,443 | Inbound |
WAF Integration in Centralised Log Management¶
Graylog collects all your web traffic activity, logs and security events.
On your “Web Application Firewall” dashboard snapshots covering the last 8 hours of web traffic activity are shown.
This dashboard is a powerful visualisation tool providing instant information on:
- List of Source IPs and Source Countries where web requests to your servers are coming from:

- WAF activity in terms of bytes transmitted and transaction times:


NOTE: This transaction time represents the time elapsed between the WAF (reverse proxy) forwarding the request to your web server and getting its response back.
- Detailed logs on all web activity:

The dashboard also includes any threat indicator as flagged by Graylog:

As part of Graylog configuration for your Web App Firewall there are also two different streams: web requests and blocked requests (traffic that was blocked by the Apache ModSec module).


